In today’s rapidly changing digital environment, Multi-Factor Authentication (MFA) has become increasingly important in protecting your sensitive data and accounts from unauthorized access. Following the feedback received on the previous article, “Why Multi-Factor Authentication as you know it is not enough in 2023“, I’ve compiled a list of MFA options, ranked from the least to the most secure.
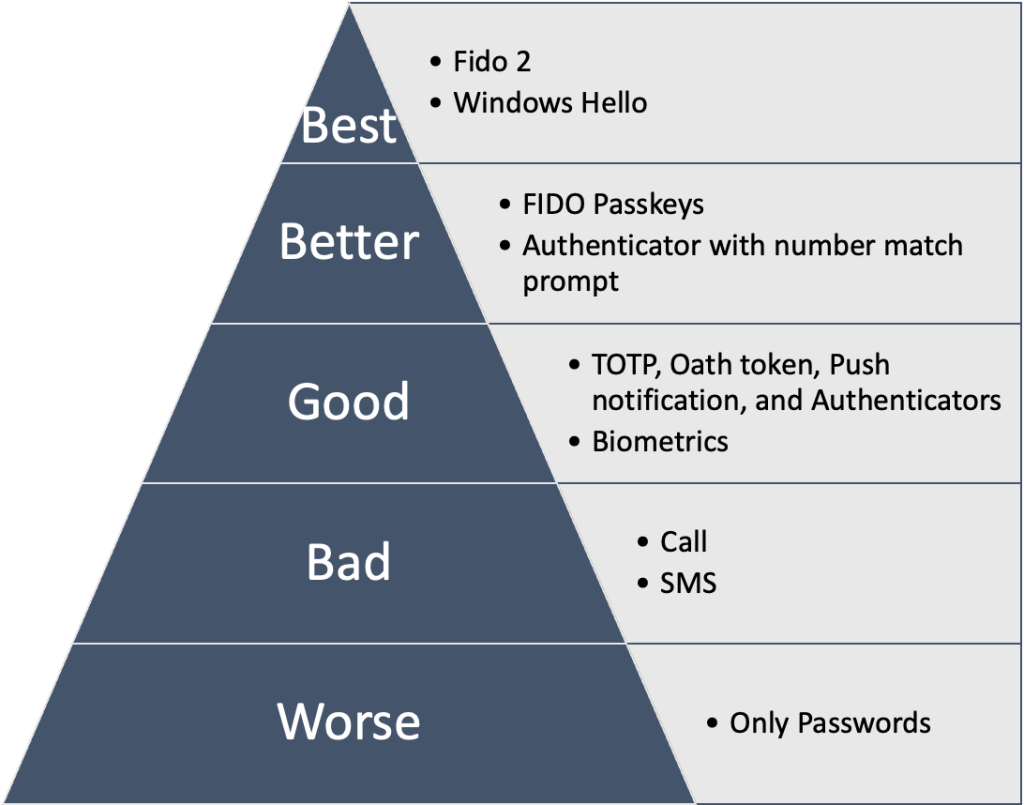
How to Choose a MFA in 2023 – MFA techniques
- Worst: Password-only authentication
Relying solely on a password for account security is the least secure option. Passwords are vulnerable to brute force attacks, social engineering, and various other hacking techniques. - Bad: Call & SMS
While better than just using a password, Call & SMS-based MFA is susceptible to channel jacking attacks and requires a phone carrier. SIM swapping and other telecom exploits can bypass this method. - Good: TOTP, Oath token, Push notification, and Authenticator apps.
These options are only susceptible to real-time phishing attacks. Push notifications and authenticator apps are slightly better but require connectivity and a smart device. They provide a higher level of security, especially when used in combination with other MFA methods.
Biometrics
Enhances security but may not always be convenient or accessible, and raises privacy concerns - Better: Authenticator app with number matching prompt, FIDO passkeys These methods are less susceptible to real-time phishing attacks but require a more sophisticated attack to be compromised. Number matching prompts and FIDO passkeys add an additional layer of security, making it harder for cybercriminals to gain unauthorized access.
- Best: Hardware-based MFA like FIDO2 and Windows Hello.
The most secure MFA options are hardware-based solutions, such as FIDO2 and Windows Hello. These methods store cryptographic keys on a physical device, providing the highest level of security against unauthorized access and real-time phishing attacks.
Additional Complementary Authentication Options
While the following options are not strictly MFA, they can complement and enhance your chosen MFA solution to create a more robust and secure authentication experience:
- Single Sign-On (SSO) and Identity Federation
streamlines authentication but requires robust security measures and for the latter also trust between participating organizations - Risk-based or Adaptive Authentication
dynamic method that can increase security while reducing the authentication burden on users in low-risk scenarios - Continuous and Behavioral Authentication
monitors user behavior and context throughout a session, detecting anomalies and signs of compromise in real-time
MFA can be hacked
While MFA offers an essential layer of security, it is crucial to remember that no security measure is foolproof, as detailed by KnowBe4. MFA can be hacked through various methods, such as phishing and social engineering attacks. Even hardware based MFA is subject to physical attacks.
To protect against these threats, organizations should consider implementing additional security measures like employee security culture (awareness, training, phishing simulations) and Identity detection and response systems. By combining MFA with other cybersecurity best practices, it is possible to strengthen the defenses and reduce the risk of unauthorized access to the systems.
Conclusion
Choosing the right MFA method is crucial for ensuring your digital assets’ safety.
By understanding the strengths and weaknesses of each option, you can make an informed decision that best suits your security needs, taking into account your specific requirements, budget, and user experience considerations. To maximize security, it’s essential to continually revise and update your authentication strategy as new threats and technologies emerge. By prioritizing the most secure methods and staying vigilant against ever-evolving cyber threats, you can effectively safeguard your digital assets and stay ahead of cybercriminals.
Stay tuned as the next article will be on AI Password cracking, role and issues of password managers and shift to password-less.
Leave a Reply