It is a pleasure to present a collaboration series of articles with Andrea Licciardi on ITDR.
As Senior Cybersecurity Manager at their Cyber Fusion Center, he spearheads proactive threat management.
Andrea Licciardi is a cybersecurity veteran with over 20 years of experienceand his encompasses security operations, risk identification, and cutting-edge defense tactics. He honed his skills at industry leaders like Leonardo and EY, where he led incident response and CERT/CSIRT services.
Moreover Andrea is a champion for AI integration in cybersecurity – he co-founded CISOs4AI (together with yours truly), a collective that advocates for AI as a game-changer in the fight against cyber threats.
Allow me to say that with Licciardi at the helm, the MAIRE Group is well-positioned for a secure and resilient digital future.
I believe that Andrea’s article will be interesting and valuable both to IT professionals and business leaders, as it offers a holistic perspective on the management of cyber threats, laying the groundwork for a stronger and more aware security culture within organizations. Our hope is that, by sharing this knowledge, we can contribute to creating a safer digital environment for everyone.
So without further ado…
Elevating Business Resilience with Identity Threat Detection and Response (ITDR)

This article stems from the need to address one of the most critical challenges in the field of cybersecurity: the protection of digital identities. Through the analysis of the Identity Threat Detection and Response (ITDR) approach, we aim to provide organizations with a broad overview of cutting-edge strategies and technologies that can be adopted to mitigate the business risk associated with cyber attacks.
The goal is twofold: on one hand, to demystify the concept of ITDR, explaining in accessible terms what it means and what benefits it can bring to companies of every size and sector; on the other hand, to provide a practical guide on how to effectively implement these solutions, highlighting the importance of a proactive approach to identity security.
Mitigating Business Risk Through ITDR: A Strategic Approach to Identity Security
The security of information has ascended to become the linchpin of organizational integrity for enterprises across the globe. As digital footprints expand, so too does the vulnerability to cyber threats that lurk in the shadows, waiting to exploit any weakness. In this dynamic environment, where data breaches are not just a possibility but a prevalent reality, their consequences resonate beyond immediate financial losses, penetrating deeply into the fabric of an organization’s reputation. It is within this context that Identity Threat Detection and Response (ITDR) stands out as a beacon of defense, offering a sophisticated arsenal against the myriad of cyber threats that businesses face today. ITDR doesn’t merely respond to threats; it anticipates them, fostering a security posture that is both proactive and resilient. By safeguarding the most crucial asset in the digital realm—the identity—ITDR empowers organizations to navigate the cybernetic waters with confidence, ensuring that they are not only protected but also positioned to thrive in the face of cyber adversity.
Business Risk in the Digital Age
The landscape of business risk has transformed, becoming inseparably entwined with the realm of information security. The surge of cyber attacks not only poses a direct threat to the continuity of business operations but also strikes at the very heart of customer trust and regulatory compliance, potentially leading to a cascade of consequences that can diminish a company’s market value. The year 2023 has shone a spotlight on a particularly alarming statistic: a staggering 40% of security breaches have been traced back to the misuse of credentials, signaling a clear and present danger to organizations worldwide. This revelation underscores a profound realization – the traditional frameworks of Identity and Access Management (IAM) are being outpaced by the cunning strategies employed by modern cyber adversaries.
In this context, a cyber attack is no longer just an interruption; it’s a significant breach that can unravel the trust painstakingly built between businesses and their customers, expose companies to severe regulatory repercussions, and erode the foundational value that underpins their presence in the market. The reliance on conventional IAM methods is being challenged, revealing vulnerabilities that contemporary cyber threats exploit with alarming efficiency and sophistication. As we navigate this new era, the necessity for advanced protective measures that can adeptly shield against, detect, and neutralize these evolving threats becomes undeniable. The digital age demands a vigilance and a strategic foresight that extends beyond the perimeter of traditional security measures, urging businesses to reevaluate and fortify their defenses in the face of an ever-changing threat landscape.
The Importance of ITDR
ITDR represents a crucial evolution in the approach to cybersecurity, focusing on the detection and response to identity-specific threats. This approach not only strengthens an organization’s ability to prevent attacks but also ensures that response measures are ready to be activated in the event of a breach, thus minimizing damage and accelerating recovery. By implementing ITDR, companies can address detection gaps between IAM and security controls, thereby filling one of the most significant weaknesses in information security.
How ITDR Mitigates Business Risk
Strengthening Preventive Controls: Through the inventory of existing controls and the audit of the IAM infrastructure to detect misconfigurations, vulnerabilities, and exposures, ITDR helps companies bolster their first line of defense against cyber attacks.
- Improving Detection: By selecting a focal point for identity alert correlation and detection logic that prioritizes identity-specific Tactics, Techniques, and Procedures (TTPs) over other detection mechanisms, ITDR enables companies to promptly identify potential threats before they can cause significant damage.
- Optimizing Response: By building or updating playbooks and automation to include IAM enforcement within the steps taken to eradicate, recover from, report, and remediate identity threats, ITDR integrates IAM incidents into response and threat-hunting processes using existing security controls in the Security Operations Center (SOC).
- Reducing Damage Impact: By rapidly implementing effective response measures, organizations can limit the extent of damage caused by a security breach, accelerating the recovery of operations and maintaining customer trust.
Data breach in 60 minutes: Acting Before It’s Too Late
Where a single compromised credential can herald a data breach in as little as an hour, the stakes have never been higher for businesses across the globe. This alarming reality underscores the critical need for organizations to adopt a robust stance against the specter of cyber threats, emphasizing the indispensability of cutting-edge security measures. Enter the realm of Identity Threat Detection and Response (ITDR), a beacon of hope in this turbulent digital sea. ITDR transcends traditional security measures by offering a proactive and strategic defense mechanism, intricately designed to detect and neutralize threats before they can inflict irreversible damage.
Imagine the scenario: the clock starts ticking the moment a cyber attacker breaches a digital perimeter. With each passing minute, the potential for widespread organizational disruption, loss of customer trust, and severe regulatory repercussions grows. In such a high-stakes environment, the speed and efficiency of ITDR systems stand as the vanguard against the relentless advance of cyber adversaries. By swiftly identifying and responding to intrusions, ITDR not only acts as a critical line of defense but also as a strategic asset, significantly mitigating the risk to business continuity and safeguarding the company’s invaluable digital assets.
In a world where digital threats are constantly evolving, becoming more sophisticated and elusive, the adoption of ITDR is not merely a recommendation; it is an imperative for survival. Through its advanced threat detection capabilities and rapid response mechanisms, ITDR equips businesses with the necessary tools to navigate the perilous waters of the digital age. It serves as a testament to the organization’s commitment to safeguarding its digital identity, reinforcing customer trust, and ensuring that operations can withstand the tempests of cyber warfare. As the digital landscape continues to expand, the role of ITDR in shaping resilient and secure business environments has never been more paramount.
Timely Response: Minimizing Financial and Reputation Impact
Speed is everything in the context of security breaches. An organization’s ability to detect and mitigate an attack before the damage spreads can make the difference between a minor inconvenience and a widespread crisis that can have significant financial and reputational repercussions. ITDR allows companies to:
- Quickly Identify Threats: With attack techniques becoming increasingly sophisticated, ITDR provides the tools to promptly detect threats, reducing exposure time.
- Respond Promptly: Through predefined playbooks and automation, ITDR facilitates a rapid and effective response, limiting the impact of attacks.
- Deep Understanding of Threats: Beyond the Surface
ITDR is not limited to mere threat detection. It also provides a deep analysis of the tactics, techniques, and procedures used by attackers, offering security teams the necessary information to:
- Prevent Future Attacks: Through understanding attack methodologies, organizations can adapt their defense strategies to prevent similar breaches in the future.
- Train and Inform Personnel: Ongoing education on new attack vectors and security best practices is crucial to maintain a resilient organization.
- Reducing Costs Associated with Breaches
A security breach can entail significant costs, not just in terms of compensation or sanctions but also regarding productivity loss and the expenses of restoring compromised systems. By implementing ITDR, organizations can:
- Reduce Direct Costs: By minimizing the impact and duration of attacks, thus reducing recovery and restoration costs.
- Avoid Indirect Costs: By protecting the company’s reputation and maintaining customer and stakeholder trust.
- A Business Imperative: Protecting Identities
Protecting the identities is not just a matter of cybersecurity but a fundamental requirement for business continuity. ITDR supports organizations in:
- Ensuring Operational Continuity: By maintaining the integrity of identity systems, organizations can ensure that critical operations remain uninterrupted.
- Supporting Compliance: By helping to meet regulatory requirements related to data protection and identity management
What ITDR Is and Is Not
Identity Threat Detection and Response (ITDR) stands as a formidable guardian, dedicated to safeguarding the very essence of digital identity. This discipline, more than a mere set of tools or processes, embodies a comprehensive approach to protecting identity infrastructures against the ever-evolving spectrum of cyber threats. ITDR transcends conventional security measures by harnessing the power of advanced threat intelligence, amalgamating it with industry best practices, a rich repository of knowledge, and a suite of sophisticated tools designed to preemptively identify, meticulously investigate, and decisively respond to any indication of compromise.
Within its operational domain, ITDR’s main function unfurls as a dynamic triad: detect, investigate, and respond. Initially, it deploys an intricate web of detection mechanisms that vigilantly monitor for the faintest whispers of suspicious activities or unauthorized changes within the identity infrastructure. This proactive surveillance is the first line of defense against the insidious attempts of cyber adversaries to undermine digital integrity.
Upon detecting a potential threat, ITDR shifts into a meticulous investigative phase, dissecting and analyzing the nature of the suspicious activity. This investigative process is not a mere cursory glance but a deep dive into the digital ether, unraveling the complexities of the threat landscape to understand the how and why behind the attack vectors.
Finally, armed with a comprehensive understanding of the threat, ITDR orchestrates a targeted response designed to neutralize the threat, mitigate any damage, and restore the sanctity of the identity infrastructure. This response is not a blunt force but a carefully calibrated action, ensuring that the digital identity fabric of the organization remains intact and resilient against future attacks.
Yet, it is crucial to understand what ITDR is not. It is not a responsibility that rests on the shoulders of a single team or department but a collective endeavor that spans the entirety of the organization’s cybersecurity framework. Nor is it limited to the confines of protecting just the Active Directory (AD); ITDR casts a wider net, safeguarding against a broad spectrum of identity threats across various IAM systems and tools. Lastly, ITDR transcends being merely a tool in the Security Operations Center (SOC) arsenal; it represents a strategic, holistic approach to identity security, integrating seamlessly with other security measures to provide a robust defense against the cyber threats of the digital age.
In essence, ITDR is the embodiment of a proactive and strategic commitment to securing the digital identity ecosystem. It is a testament to an organization’s resolve to not just defend against, but to anticipate and neutralize threats, thereby ensuring the digital trust and continuity that are the bedrock of success in the digital age.
What ITDR Is:
- A proactive and reactive approach to identity security.
- Complementary to existing solutions like Network Detection and Response (NDR) and Endpoint Detection and Response (EDR), with a specific focus on identity infrastructure.
- A unifier of tools and best practices to protect the integrity of identity systems, also essential for mature IAM and infrastructure security implementations.
What ITDR Is Not:
- The responsibility of a single group; ITDR is a shared responsibility among IAM and infrastructure security teams.
- Limited only to Active Directory (AD) security; ITDR includes detection and response to AD threats but goes beyond, covering a broader set of identity threats across various IAM systems and tools.
- A SOC tool; tools like SIEM, SOAR, and XDR are active parts of a cohesive ITDR strategy, but most vendors in these markets lack the capability to detect identity threats based on user behavior rather than TTPs.
Prevention, Detection, and Response: Where ITDR Fits
- PreventionThis is the first line of defense, focused on preventing attacks before they happen. It includes controls such as MFA, vulnerability management, and secure infrastructure configuration. While fundamental, prevention alone is not enough to stop all threats.
- DetectionWhen preventive measures are bypassed, detection comes into play. Timely threat detection allows organizations to identify and isolate attacks before they can cause significant damage. ITDR positions itself here, offering an identity-focused mechanism to detect threats that might otherwise go unnoticed.
- ResponseOnce a threat is identified, the response phase aims to mitigate the impact of the attack, eradicate the threat, and restore systems to their normal operational state. ITDR integrates identity threat response into existing response and threat-hunting processes, using security controls present in the Security Operations Center (SOC).
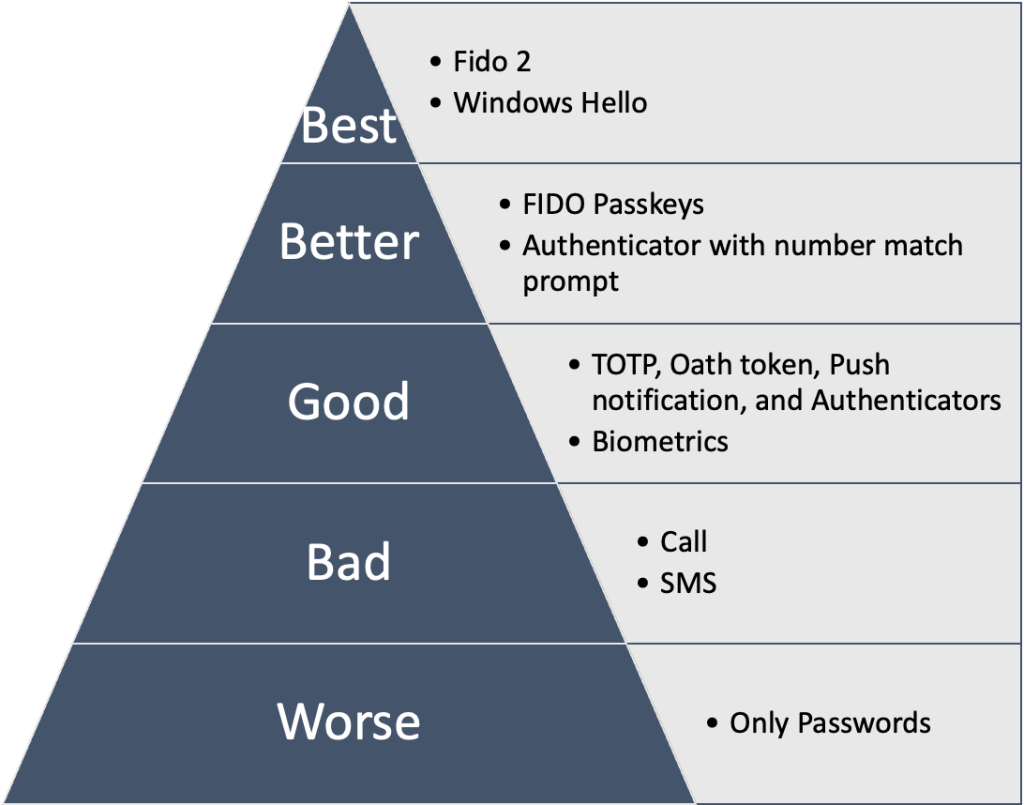
The Importance of ITDR in an Advanced Authentication Context
- Advanced Threat Detection: Even the most advanced passwordless and MFA technologies can be vulnerable to sophisticated tactics, such as social engineering or advanced phishing attacks. ITDR enables the detection of these advanced threats by monitoring unusual behaviors or suspicious access attempts.
- Prevention Completion: While MFA and passwordless raise the barrier against unauthorized access, ITDR complements this scenario with an additional layer of security, allowing organizations to quickly identify and respond to attacks, potentially reducing damage.
- Flexibility in Response: With attack techniques continuously evolving, ITDR provides organizations with the necessary flexibility to quickly adapt their response strategies, ensuring constant protection against new vulnerabilities and attack methods.
Prevention, Detection, and Response in the Passwordless and MFA Context
- Prevention: MFA and passwordless act as robust preventive mechanisms, significantly increasing the difficulty for an attacker to gain unauthorized access.
- Detection: ITDR comes into play when preventive measures are not enough, detecting suspicious identity-related activities that could indicate an attempt to bypass security measures.
- Response: Once a threat is detected, ITDR facilitates a coordinated response, helping to mitigate the attack and restore the security of the identity infrastructure.
ITDR and Artificial Intelligence: A Strategic Alliance for Identity Security
The fusion of Artificial Intelligence (AI) with Identity Threat Detection and Response (ITDR) emerges as a beacon of innovation, casting new light on the battleground of cybersecurity. This era, marked by an explosion of AI-driven technologies, has ushered in transformative changes across myriad sectors, with cybersecurity standing at the forefront of this revolution. The integration of AI into ITDR is not just an addition to the arsenal against cyber threats; it represents a paradigm shift, promising to enhance the effectiveness and efficiency of how digital defenses are orchestrated.
This strategic alliance between AI and ITDR transforms the landscape of digital identity protection. It amplifies an organization’s ability to preempt, detect, and neutralize cyber threats with unparalleled precision, thereby fortifying the bastions safeguarding digital identities. This synergy does more than just augment detection and response mechanisms; it heralds the dawn of new horizons in the realm of digital identity security, promising a future where the sanctity of digital personas is preserved against the ever-evolving threats that roam the cyber ether.
Enhancing Threat Detection with AI
The application of AI in ITDR radically transforms how threats are identified. AI-based solutions are capable of analyzing vast volumes of data in real-time, learning from attack patterns and continuously adapting to identify suspicious behaviors with unprecedented precision. This approach offers significant advantages:
- Proactive Detection: AI can identify subtle signals of imminent attacks, allowing organizations to act preventively.
- Minimization of False Positives: Thanks to the ability to learn from data, AI constantly refines its detection criteria, reducing unjustified alarms that can overwhelm security teams.
- Rapid and Automated Response
Integrating AI into ITDR not only improves threat detection but also the speed and effectiveness of responses. AI solutions can automate many actions required to mitigate a threat, from isolating compromised systems to resetting access credentials, to notifying relevant teams. This allows for an almost instantaneous response that can mean the difference between a contained incident and a disastrous breach.
Predictive Analysis and Continuous Learning
One of the most transformative aspects of using AI in ITDR is its capacity for continuous learning. By constantly analyzing past and present attacks, AI not only improves its detection and response capabilities but can also anticipate future trends and emerging vulnerabilities. This predictive approach enables organizations to:
- Adapt Defense Strategies: By anticipating attackers’ moves, companies can proactively strengthen defenses in the most critical areas.
- Targeted Training: With a deeper understanding of the most likely attack techniques, organizations can develop more effective training programs for their staff.
- Beyond Security: AI as a Strategic Ally
The integration of AI in ITDR goes beyond the technical aspect of security. It supports a broader strategic vision that includes:
Resource Optimization: By automating detection and response functions, AI frees up valuable resources that can be reallocated to broader strategic initiatives.
Data-Driven Decisions: AI provides valuable insights from security data analysis, supporting business decisions with concrete and timely information.
Conclusion
The adoption of ITDR (Identity Threat Detection and Response) solutions represents a fundamental pillar for the security strategies of organizations in the digital age. Through a proactive and reactive approach, ITDR not only strengthens defenses against the continuously evolving cyber threats but also ensures a rapid and effective response in the event of incidents, mitigating business impact.
Summary of Key Points:
- Mitigating Business Risk: ITDR is essential for addressing the challenges posed by modern threats, offering a holistic approach that protects the integrity of digital identities and maintains the trust of customers and stakeholders.
- The Importance of Prevention, Detection, and Response: Through the integration of robust preventive controls, advanced detection mechanisms, and agile response strategies, ITDR provides an unprecedented level of protection against security breaches.
- Synergy with Advanced Technologies: The incorporation of artificial intelligence (AI) into ITDR amplifies detection and response capabilities, allowing organizations to anticipate and neutralize threats before they can cause significant damage.
ITDR is not just a technical response to cyber threats but a critical business strategy that safeguards operations, reputation, and business continuity. Implementing ITDR means adopting a visionary approach to security, recognizing that the protection of digital identities is fundamental for long-term success and growth.
Organizations should therefore consider ITDR not as a cost, but as an investment in their future resilience and sustainability. With the right commitment to implementing and optimizing ITDR solutions, companies can not only navigate safely through today’s complex and rapidly evolving digital landscape but also position themselves to thrive in an increasingly interconnected and technology-dependent future.
But Wait, There’s More!
This dive into ITDR is just the beginning. We’ve got more up our sleeves, so stay tuned for follow-up articles where we’ll explore new strategies, dive deeper into AI’s role in cybersecurity, and share real-world success stories. The world of ITDR is vast and ever-evolving, and we’re here to guide you through it, every step of the way. Keep an eye out—there’s plenty more where this came from!



Recent Comments